Dev Log 10: Lockpicking and Hacking
Hi guys,
It has been exactly two months since the last dev log, which is also the shortest interval between two log entries this game has ever seen. We've been developing very rapidly and there's a lot to show, but for now I'm going to focus on lockpicking and hacking mechanics.
That I decided to make these mechanics more complex should come to no surprise to the people that have been following the development of our games. When I originally shared a sneak peak of lockpicking on X it caused a bit of a controversy. It is well known that among the menagerie that is the RPG gamer collective, "minigames" are not look upon with favor. I think this is mostly due to the concrete implementations and not so much the concept. However, I want to take a step back from "minigames" completely and argue that it is not what Infusion's lockpicking and hacking mechanics are, but are instead just normal gameplay mechanics that are being elaborated to a level of detail that is not traditionally seen in RPGs.
I will concede, however, that there are elements of our implementation that could be considered "minigamey", but I would say that is inevitable whenever you try to engage with some real-world mechanism that is too complex and needs some amount of simplification and abstraction in order to transform it into an engaging game mechanics.
First, let me explain the fundamentals of these new mechanics.
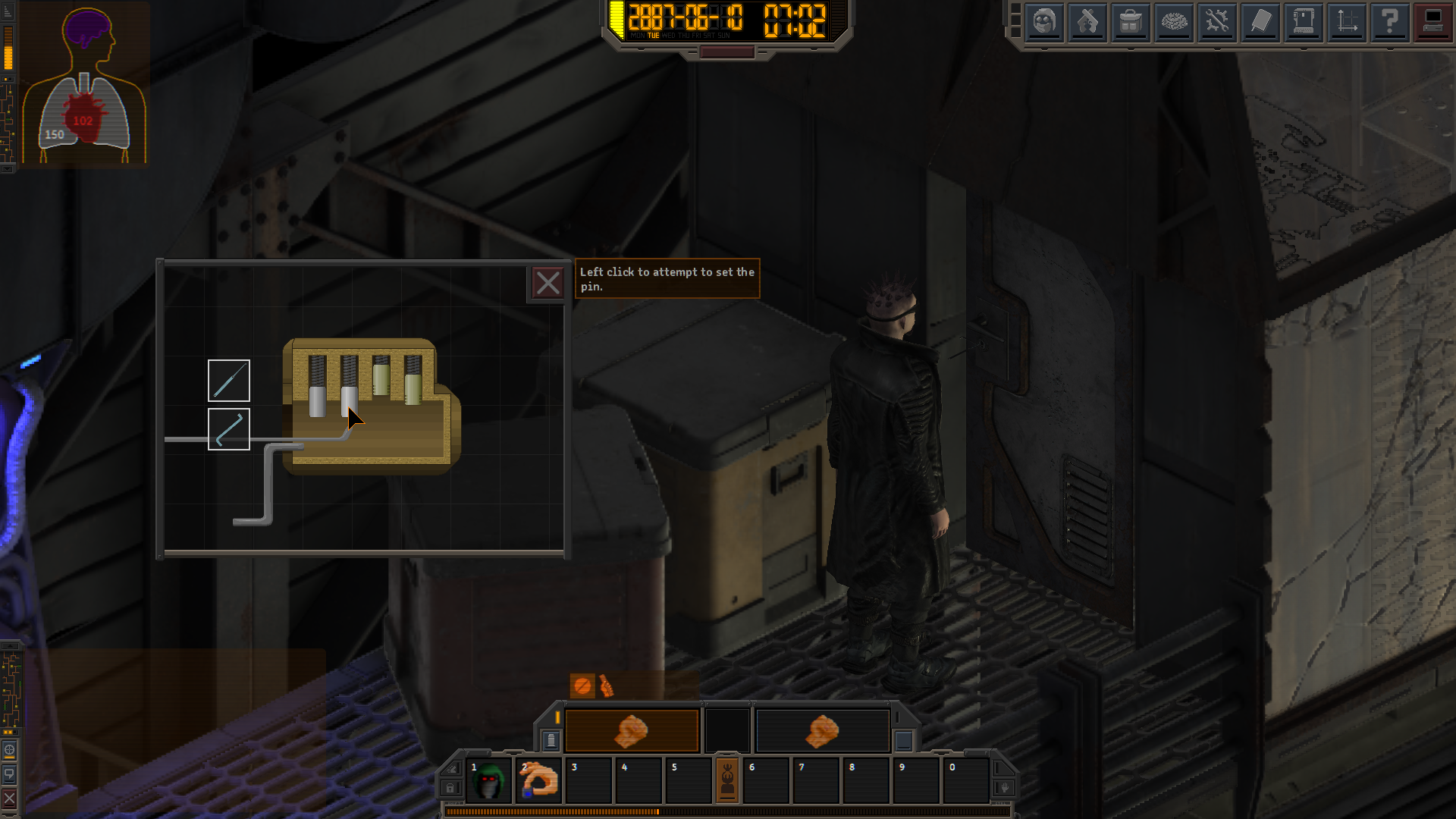
In Infusion, you'll pick the mechanical locks of doors, safes and containers manually, using tools such as lockpicks and tension wrenches. Locks will vary in type and configuration. On the screenshot you can see a typical pin tumbler lock, that I'm sure you're used to seeing in your average medieval walking simulator RPGs. It sports two types of pins that behave just a bit little differently.
In order to pick this lock, you'll have to tinker with it a bit and figure out the wrench tension at which all the different pins are set. This will require a bit of patience and paying attention to visual cues. The more skill you have in hacking, the more obvious these cues are and also you have to be less precise with the alignment.
Once you get a feel for this type of lock and learn the particularities of different pin types, and as long you keep investing into your lockpicking skill and some quality lockpicks, you should start getting quite good at this. But, don't worry, we'll introduce different, more complex, lock types as the game progresses, such as the disk detainer lock. These will become more complicated to solve, but we'll also provide you with more tools that can assist you.
If this sounds appealing and you choose to go down the lockpicking path, by the end of the game, both you and your character should feel like seasoned burglars. Lockpicking (and hacking especially) is no longer going to be just a simple numerical check, but will instead try to immerse you into a role of a professional lockpicker.
This is the point of this mechanic, as well as of all the new mechanics and complexities we're bringing into Infusion - we want the player to have a distinct experience based on skills, feats, gear, and chosen play-style. We want them to feel like they are their character.
On the other hand, if you don't like lockpicking (or any other mechanic), don't worry, we'll have plenty of other things for you to do. In Infusion. Lockpicking will not be as dominant of a skill-check as in Underrail 1. A lot of times you'll be able to circumvent, cut, smash or shoot your way through a locked door. Lockpicking is oftentimes going to be just one of the ways to solve a problem and the exclusive content here will probably be limited to a number of higher end safes that do not have keys anywhere in the game.
Also, because lockpicking is a slower and more involved action now, we'll be sure to distribute the locked objects more sparesly with higher concentration of loot and other rewards behind individual locks.

Hacking is somewhat of a bigger beast. Actually, hacking is just a part of the new computer system.
For the purposes of the game, I implemented a simple operating system inside the game and a command shell on top of it you can use to interact with it. And to use the shell, you'll going to need a keyboard and a monitor, which both have actual implementations in the game. For now, those function perfectly, but later I'll start removing keys from some of those and maybe shading in some dead pixel areas on the monitor as an added layer of suffering immersion, randomly I think (have fun doing anything in command shell without the A key and a crack down the middle of the monitor).
Also most of the computers in the game are going to be connected into a single network and you'll be able to access them remotely and you'll be able to share files with NPCs, and they will sometimes hack into your computers....
Now, you may think I've gone off the deep end with these features, but I intend to go even further. I'm yet to make a graphical UI for applications that are going to run on these computers and more. The reason I'm doing all this (apart from that it's fun) is so we can use this system to implement any kind of machine and computer interaction that we want seamlessly into the game. In Underrail 1 we mostly relied on the dialog system for this and it was very limiting and clunky. In the long run, I believe, my work on these features is going to pay off tenfold.
So what can you do in this new computer system:
- Browse files, copy them to your own personal computer, sometimes sell them to information brokers
- Control doors, gates and various machinery that's connected to the system
- Obtain new software, including new hacking tools
- Install new hardware and software on your personal (hand-held) computer that will give you new gameplay functionalities, such as motion tracking radar
- Communicate remotely with other people
- And more
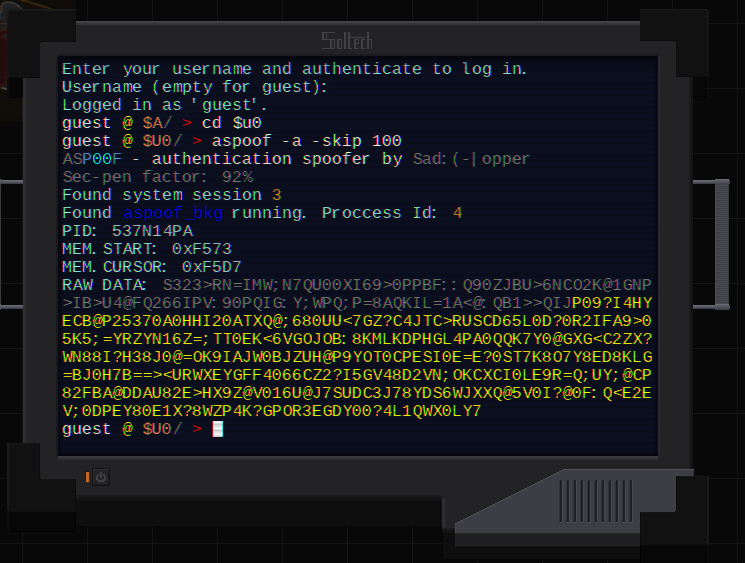
When it comes to hacking itself, it will be similar in lockpicking in some ways. Your success will depend on your knowledge of the hacking software, its quality as well as your hacking skill. Your software's version (quality) grants you a bonus to your hacking skill check, but may also act as hard requirement to getting past some security measures. E.g. you'll not be able to beat mid-game encryption software using early-game decryption software, regardless of your skill, so you're expected to keep up with your software quality throughout the game.
When your combined hacking skill is not quite enough to hack something smoothly, you'll usually be faced with some sort of raw stream of data you'll have to make sense of in order too boost your check. Various additional software might come in handy here.
Later, I intend to make some graphical tools a less hardcore hacker might use instead of the command shell, but the latter will always provide you with most effective hacking skill and the greatest variety of tools.
Like with lockpicking, there is an idea here of sort of becoming an actual hacker within the game's world. The computer system implemented here is no minigame, it's something that exists and runs within the game's world at all time and its workings are part of the lore and aesthetic in the game.
* * * * * * *
The way we handled lockpicking and hacking is the way we're going to go about most of the mechanisms (machines and such) in the game. We're not going to use dialog for anything else but the actual dialog. Whenever we require some intricate interaction with a machine or an item we're going to implement interfaces in the vein of those seen above, using computer system where appropriate.
You can also tell we invested a lot into the minute details. You can see what's on the computer monitor even without opening its interface. With the big enough display, you could actually read the text. This is a separate engine feature that we can use to render all kinds of dynamic displays in the game, which is important considering what we plan to do with the environmental story-telling.
Also, you can see when a lockpick or key are left in a lock. The appearance of the lock is going to correspond with the lock type. You can see the exact data storage device (USB-like thing) that's currently inserted into a computer, and so on.
We have a general design philosophy when it comes to these things - we believe that the narrative, the aesthetic (audio-visual) and the mechanical (gameplay) aspects of some part of the game should be closely integrated and so amplify and feed-off each other. We believe this maxes out the immersion and gives the player the most authentic experience.
* * * * * * *
That's it for now. Let me know how you like these new systems and stay tuned for more dev logs. In the meantime, follow me on X, where I post smaller tidbits of development regularly.
Cheers!



